Half of the .nl domain’s DNS infrastructure now protected by RPKI
Routing hijacks are a threat to the availability and reliability of the DNS and other services. A successful hijack can make a domain’s name servers unreachable or cause DNS queries to be diverted to malicious servers. And configuration errors or ‘fat fingers’ can have much the same effect as deliberate hijacking. Fortunately, many such problems can be avoided by using Resource Public Key Infrastructure (RPKI). In this article, we look at how well deployment of RPKI is going in the networks of second-level .nl name servers.
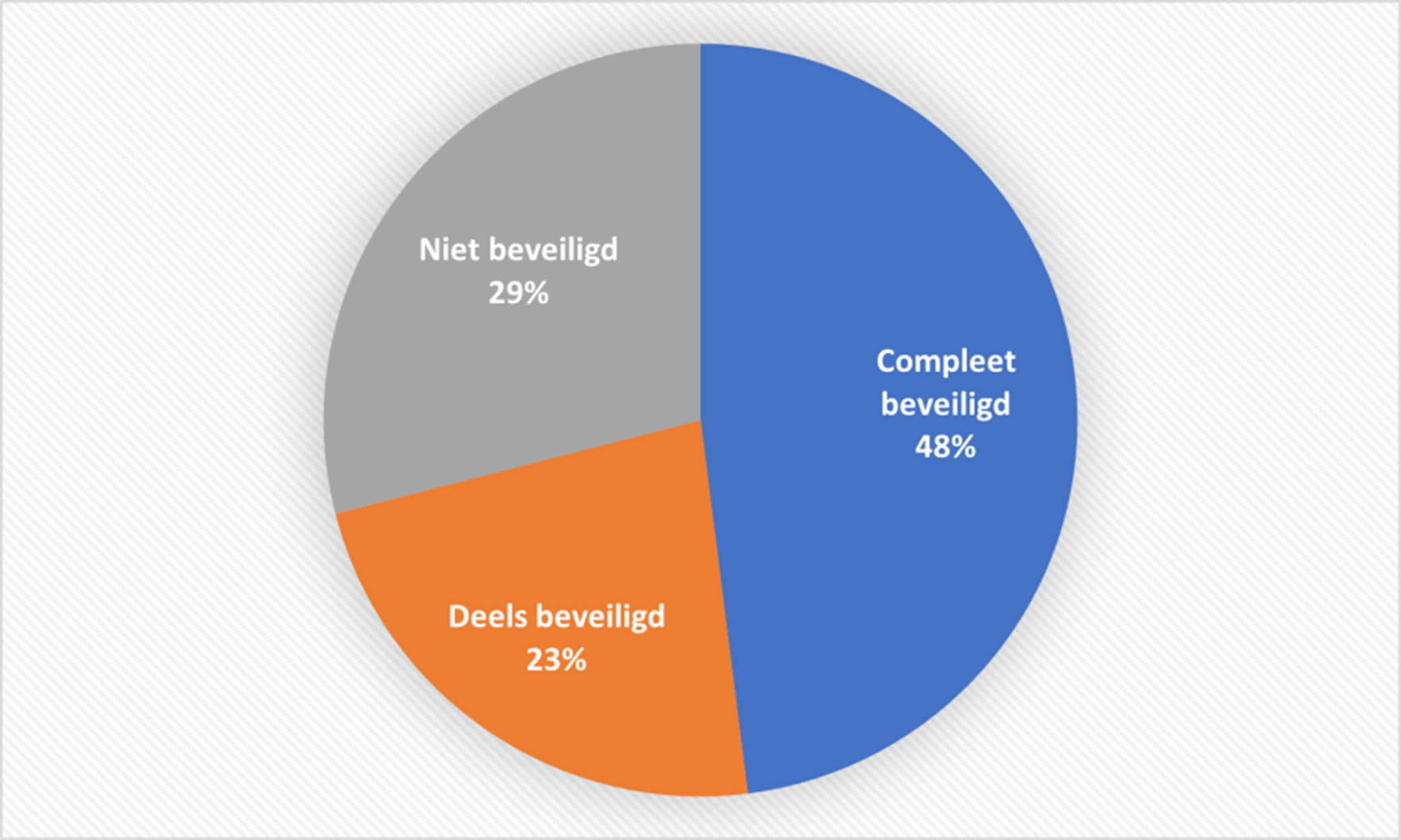
Figure 1: Percentages of .nl domains with no/some/all name servers on RPKI-enabled networks on 19 January 2021. Current data available from stats.sidnlabs.nl.
What is a route hijack?
A route hijack involves the diversion of internet traffic to a network other than the one it was intended for. Hijacking is possible because the Border Gateway Protocol (BGP) wasn’t developed with security in mind. Defined back in 1989, the BGP determines the routes that internet data flows take from source to destination. Here’s an example of how route hijacking works. The malicious network AS64496 sends out messages claiming that it operates the IP address range 192.0.2.0/24, which is actually on the AS65551 network. Having received AS64496’s messages, internet-connected routers that are closer to AS64496 than to AS65551 are tricked into sending traffic destined for addresses in that range to the malicious network. In practice, it’s common for traffic to be misdirected because of configuration errors as well. See @bgpstream, for example. Although there’s no malicious intent in such cases, the effect is much the same. If the name server for the domain example.nl is reachable at the address 192.0.2.1, a hijack can have serious consequences. By setting up a malicious name server at the same address, an attacker can provide false information in response to DNS queries about example.nl. That is not merely a theoretical possibility. In April 2018, attackers used that very technique to hijack some of cloud service provider Amazon’s DNS traffic. Innocent configuration errors are less likely to result in traffic ending at the wrong place, because there won’t usually be a name server at the relevant address, capable of providing information about example.nl. So, instead of being diverted, traffic simply won’t be able to reach example.nl and its services.
What is RPKI?
Resource Public Key Infrastructure (RPKI) is a security extension to the BGP, which enables the owner of an address range to use public key cryptography to publish the identity of the AS(es) on which the addresses are reachable. So, in our previous example, the owner of 192.0.2.0/24 could use RPKI to indicate that the addresses are reachable on AS65551. That would involve publishing a Route Origin Authorisation (ROA) listing all the ASs from which the addresses may be advertised. Then a router that receives a message saying that 192.0.2.0/24 is reachable at AS64496 can check the ROA to see whether AS64496 is listed as an authorised AS. If it isn’t, the message can be ignored. However, RPKI doesn’t protect against AS64496 pretending to be on the path to AS12345 (192.0.2.0/24). ASPA (Autonomous System Provider Authorization) may resolve that flaw, but isn’t yet ready for use.
Our research
Since December 2020, we have been publishing daily information on stats.sidnlabs.nl about how many .nl domains have name servers with RPKI-enabled IP addresses. Domains whose name servers are all RPKI-enabled are in principle protected against configuration errors and the simple route hijacking tactic described above. However, the protection is effective only where the router looking for an RPKI-enabled domain validates the signature in the domain’s ROA. A further complication is that some domains have one or more name servers with RPKI-enabled addresses and one or more without. Such domains are only partially protected. For our analysis, we perform a daily check on the name servers and corresponding IP addresses of all .nl domains. The data is obtained from the OpenINTEL project. Using data from a route collector, we establish the prefix for the IP address of each name server and the AS(s) from which the prefix is advertised. That information can then be used to determine whether the prefix is protected with RPKI. That’s done using Routinator, an RPKI validator developed by NLnet Labs. Routinator can also tell us whether an AS’s advertised prefix is inconsistent with a domain’s ROA.
Almost half protected
As figure 1 shows, on 19 January 2021, 48 per cent of .nl domains were using name servers whose IP addresses all had ROAs. That’s up eight percentage points since eight months earlier. A further 22 per cent of .nl domains had at least one name server with an ROA. Amongst popular domains, the use of RPKI is slightly higher still. We measure the popularity of a domain using the DNS Magnitude method, which involves estimation on the basis of DNS queries. When we looked at the thousand most popular .nl domains thus identified, we found that 53 per cent had name servers with ROAs. Even when analysis is extended to the 100,000 most popular .nl domains, the ROA rate is still 49 per cent.
DNS service providers have a big influence
Many domains use name servers operated by DNS service providers or registrars. Therefore, if a service provider or registrar has an RPKI-enabled network, all their customers’ domains will be protected. Unfortunately, many such networks aren’t yet protected. Of the ten name servers responsible for the most .nl domains, seven have no RPKI protection. And those name servers account for 33 per cent of all .nl domains. Therefore, if the operators of the servers in question were to enable RPKI on their networks, it would have a major positive impact on the security of .nl.
DNSSEC & RPKI: a good combination
Of course, the discussion of DNS security inevitably leads to DNSSEC. DNSSEC and RPKI are mutually complementary security standards. If an attacker performs a routing hijack in order to impersonate a domain’s name server, a validating DNS resolver can detect the abuse, as long as the domain name is DNSSEC-enabled. However, DNSSEC doesn’t protect against a name server being rendered unreachable by a routing hijack. RPKI does offer a partial solution, though. According to our research, 23 per cent of all .nl domains have both DNSSEC and RPKI enabled. On the other hand, 8 per cent of domains don’t support either of the two standards. Responsibility for rolling out RPKI lies with network operators, but a domain’s network operator is often not the same company that operates the domain’s name servers. Consequently, the use of DNSSEC doesn’t necessarily mean that RPKI is enabled as well. As well as enabling RPKI, an operator can use multiple name servers and distribute them across multiple networks. Then, if a network is unreachable – following a route hijack, for example – a DNS resolver can still send queries to one of the other name servers. All .nl domains have at least two name servers, but more than 44 per cent of them have all their name servers on the same AS. However, a very high proportion – more than 80 per cent – of those name servers are on networks with ROAs.
What can be done to increase RPKI deployment?
As this article makes clear, there is ample scope for improving RPKI deployment in networks that host DNS infrastructure. One way of significantly increasing deployment would be to persuade big DNS service providers and registrars to locate their name servers on networks with ROAs. If you’d like to know whether your name server’s network is RPKI-enabled, you can use the tool on stat.ripe.net, for example. All you need is your name server’s IP address. Extensive RPKI rollout is of little value, however, unless routers actually reject bogus routes. Otherwise, end users are not protected. Unfortunately, an initial study indicates that there is a long way to go in this regard as well.
DNS isn’t enough
If you have a domain name that is used for a website, for example, your name servers are not the only security consideration. If the network hosting your webserver is hijacked, the impact can be at least as serious as an attack affecting your name servers. We therefore plan to follow up this article with a piece about our research into the use of RPKI to protect the webservers for .nl domains.
This message is taken from SIDN Labs, read the entire blog here