SIDN Labs and SURF have released a new version of the DDoS Clearing House in a Box, a system that enables network operators to automatically share details of the DDoS attacks they handle, in the form of ‘DDoS fingerprints’. In this blog, we briefly outline our improvements and how they contribute to the trials we’ll be carrying out in the Netherlands and Italy.
Anti-DDoS Coalition and CONCORDIA
SIDN and SURF are proud to be part of the Dutch Anti-DDoS Coalition as well as of the CONCORDIA project, where we work on mechanisms and tools that enable service providers to handle DDoS attacks more proactively. Both projects involve numerous organisations including governments, internet providers, internet exchanges, academic institutions, non-profit organisations and banks.
An important building block in both projects is the DDoS Clearing House, a shared system that enables participating service providers to automatically share the characteristics of DDoS attacks they handle in the form of so-called ‘DDoS fingerprints’. The tenet here is that to be forewarned is to be forearmed. Sharing DDoS fingerprints with other participants warns them that new attacks may be underway and extends the DDoS mitigation services that participants already have in place, such as scrubbing services like the NaWas. Comparing attacks currently in progress with attacks whose details are already recorded in the Clearing House can also provide pointers as to the best way to mitigate ongoing attacks.
Recent developments show that DDoS attacks are still very much an issue and – more worryingly – are increasing in size, making our work with the DDoS Clearing House all the more relevant and pressing.
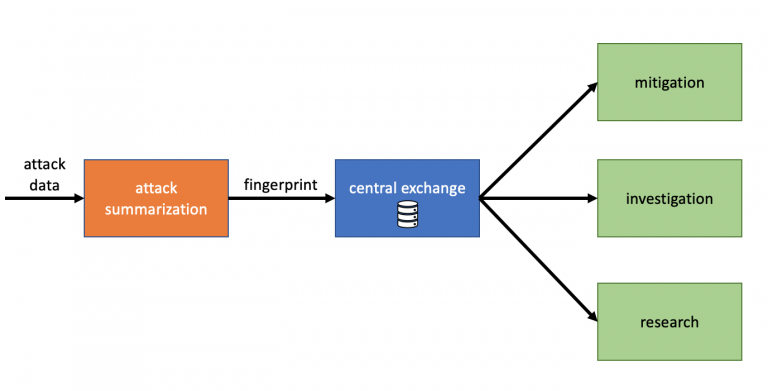
Figure 1: Clearing House overview.
We have been working on the DDoS Clearing House since the beginning of 2019, during which time various milestones have been reached, such as:
- Legal agreements in order to share DDoS fingerprints between partners (developed by the Dutch Anti-DDoS Coalition)
- DDoS drills performed against a monitored infrastructure (carried out by the Dutch Anti-DDoS Coalition)
- Software specification and prototype development (carried out in both projects at the same time)
We provided a much more extensive description of the Anti-DDoS coalition and the DDoS Clearing House as well as our goals and experiences in a three-part series of blog posts on the CONCORDIA website published earlier this year:
- Increasing the Netherlands’ DDoS resilience together
- Setting up a national DDoS clearing house
- Dutch Anti-DDoS Coalition: lessons learned and the way forward
Clearing House core components
The software components are run locally by groups of service providers who collaborate to fend off DDoS attacks, such as the members of the Dutch Anti-DDoS Coalition.
Figure 2 shows that each service provider (called a “collaborator”) will have their own local fingerprint database, called DDoSDB. Their operations teams decide what fingerprints to share with the central repository, which runs at a neutral location and aggregates DDoS fingerprints from all the collaborators.
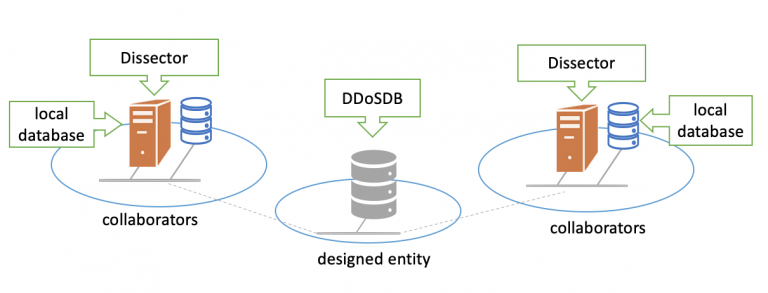
Figure 2: Clearing House core software components.
Improvement #1: more accurate DDoS fingerprints
Dissector: is the software responsible for analysing network traffic (pcap) and extracting attack characteristics. This new release incorporates new statistical methods that make the process of generating fingerprints smoother and faster.
Improvement #2: better visualisation of DDoS attacks
DDoSDB: is the repository responsible for getting DDoS fingerprints and sharing them among the partners. We have developed new visualisation pages and improved the software stability. We have also added the ability to annotate fingerprints to provide additional (human-readable) information about the fingerprints themselves or the attacks they represent. Annotations can be made or edited by the submitter of the fingerprint or the administrator of the DDoSDB.
Improvement #3: automatic updates
DDoSDB in a Box: is a virtual machine where we place all the components together and configure them. The goal is to make it easy to test the software and to go through the whole cycle of DDoS processing. In addition, the DDoSDB in a Box concept makes it easier to operate the Clearing House in a distributed mode, eventually perhaps without the central DDoSDB instance. The new version of the software is already available and now also has an automatic software upgrade in place, meaning that instances of DDoSDB in a Box are automatically upgraded when new software component releases become available. That in turn allows users of the virtual machine to keep their systems (and databases) up and running using the latest software version.
Improvement #4: better description of the components
Last but certainly not least, we have cleaned up the repositories and improved the documentation that goes along with them. That is especially important for people just trialling or starting to use the DDoS Clearing House and its components. For developers wanting to contribute to the components, the improved development guidelines provide clear instructions on how to set up an instance on their own development system. We also have several screencasts showing how to run the software components.
Contribute
We are happy with the results secured so far, and along the way have gotten a better understanding of all the things we still need (and want) to improve. That is why we are sharing details with the community and encouraging people to try it out for themselves and for developers to contribute. You can find our software at https://github.com/ddos-clearing-house.
Acknowledgments
SIDN and SURF were partly funded by the European Union’s Horizon 2020 Research and Innovation program under Grant Agreement No 830927. Project website: https://www.concordia-h2020.eu/
This message is taken from SIDN Labs, read the entire blog here.